LIBRARY CREDIT EXCHANGES
Coinomi, under the pressure of the community (to whom I extend my special thanks), has finally released an official statement concerning the incident. You can find their statement at this link (I've also provided a screenshot for reference):
https://medium.com/coinomi/official-statement-on-spell-check-findings-547ca348676bFirstly, I wish they would display the same level of transparency that I have shown by publishing my responses on their social media channels, allowing readers to make their own judgements based on both sides of the story.
I had anticipated that Coinomi's official statement would be lacking in some areas, but I did not expect it to be as inadequate as it turned out to be. However, it seems to be a clear reflection of the mentality behind their proclaimed "never been hacked" wallet.
I will now address their official statement, quoting and providing screenshots of parts of their response. This seems necessary, given their tendency to delete their posts.
TOKENGUARDIAN EXCHANGE
Starting with their announcement title:

Referring to this severe security issue as merely "findings" is not only misleading, but it also demonstrates an evasion of responsibility. Coinomi appears to be hesitant to label this issue as a critical vulnerability, even though its seriousness extends beyond just 'critical.' In the field of information security, vulnerabilities are typically ranked according to their severity: Low, Medium, High, or Critical. Given the gravity of this situation, I propose that the information security community introduce a new ranking - the "Coinomi Level," which would denote the highest level of severity.
Going to the next statement:
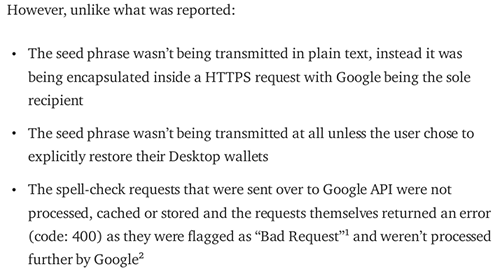
"The seed phrase wasn’t being transmitted in plain text, instead it was being encapsulated inside a HTTPS request with Google being the sole recipient"
When I mentioned that my passphrase was transmitted in plain text, I was referring to the fact that it reached Google API servers without any form of encryption. It is essential to understand the difference between transmitting data through a secure tunnel (as is done with HTTPS) and actually encrypting the data before transmitting it.
Hypothetically speaking, if Coinomi had encrypted the passphrase prior to sending it to Google, then even if this data was transmitted via HTTP (without SSL/TLS), it would still have reached the destination in an encrypted format. The notion of securely transmitting my unencrypted passphrase to Google under the guise of taking all necessary security measures is rather amusing, if not alarming.
“The seed phrase wasn’t being transmitted at all unless the user chose to explicitly restore their Desktop wallets”
Coinomi's statement is rather humorous, essentially implying, "This isn't a vulnerability because the issue only arises when the user chooses to restore their wallet. Otherwise, they would be safe." This suggests that, as a Coinomi user, you're not supposed to use the "restore your wallet" feature, and that this option exists solely to spell-check your passphrase against Google's dictionary.
"The spell-check requests that were sent over to Google API were not processed, cached or stored and the requests themselves returned an error (code: 400) as they were flagged as “Bad Request”¹ and weren’t processed further by Google"
Coinomi's claim is somewhat misleading. How can Google's API server respond with a "Bad Request" without first understanding the content sent to it? The screenshot Coinomi provided, showing Google's web service response, is actually from the perspective of the web application. A web application doesn't respond to a request until it first processes the data and determines its validity.
In reality, the situation might be much worse than Coinomi is implying. Google's API servers require a valid API Key to use their web services. In Coinomi's case, they sent the request using an invalid (unauthorized) API Key, causing Google's API server to treat the request as a bad request. This would likely alert Google's team to investigate the cause of the bad request. Upon seeing the 12 English words separated by spaces (which looks like a passphrase to a cryptocurrency wallet), they might start to question its origins. This situation becomes even more concerning if the server is managed by a third party or has been compromised.
In other words, if Coinomi had used a valid API Key, Google would have been obligated to handle the data more responsibly. This could potentially make anyone attempting to misuse the passphrase think twice.
Going to the next statement:
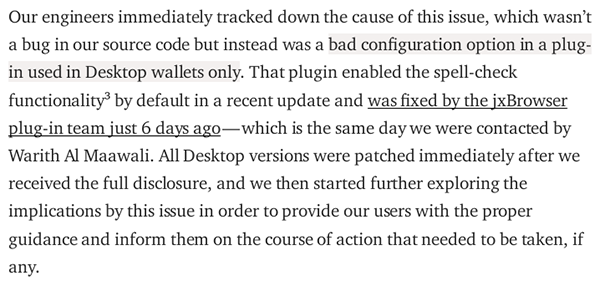
"Our engineers immediately tracked down the cause of this issue, which wasn’t a bug in our source code but instead was a bad configuration option in a plug-in used in Desktop wallets only."
Claiming that this issue wasn't part of their "source code" is quite misleading, and it appears that Coinomi is attempting to evade responsibility. The JxBrowser component/plug-in is bundled with Coinomi’s wallet at the source code level, and developers have the ability to enable or disable any undesired feature of JxBrowser directly from the source code. Essentially, this was a feature that Coinomi misused, and it consequently turned into a critical security bug.
Coinomi’s team seems to be trying to divert the community's attention and place the blame on JxBrowser for their own mistakes. However, it's worth noting that JxBrowser clearly explained this default behavior in their documentation as early as 2016, and provided instructions on how to disable it:
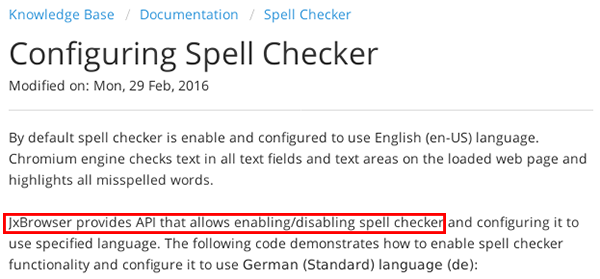
The original link can be found here:
https://jxbrowser.support.teamdev.com/support/solutions/articles/9000044250-configuring-spell-checker
To make it simple for the readers, Coinomi could have avoided the “spell check” scandal with a single line of code:
spellChecker.setEnabled(false);
It seems that the developers at Coinomi, whom they refer to as the "Code Gurus," did not take the time to familiarize themselves with the JxBrowser documentation. It is puzzling why they even chose to use JxBrowser in the first place. The core functionality of the Coinomi wallet is already based on the Java programming language, which inherently provides cross-platform compatibility. There should have been no need for a third-party component like JxBrowser. The likely explanation is that they were too lazy to develop the UI natively in Java and opted for a quick and hasty solution to release the Desktop version promptly, possibly disregarding proper quality assurance testing, assuming it was conducted at all.
USDE LOGIN
The interesting aspect of the "spell check" vulnerability, when viewed from a legal perspective, is that it could be considered a "feature" or, more specifically, a hidden feature. Coinomi did not disclose this feature anywhere in their "Terms of Use," their wallet application, or their documentation.
Now, let's discuss the terms and conditions of using the Google API. You can find these terms in the following links:
https://developers.google.com/terms/
https://developers.google.com/terms/api-services-user-data-policy
Quoting some of their terms:
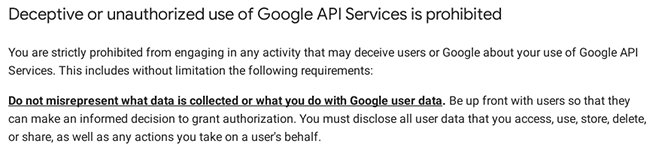
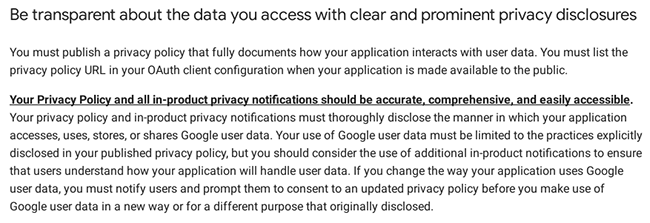
It is evident that Coinomi has violated several terms and conditions in their actions. For instance, they utilized the Google API without a valid API Key, which constitutes (unauthorized usage) usage, and they failed to inform their users about this practice. In essence, they deceived Coinomi wallet users by implementing a hidden "spell check" feature that relies on Google API servers to verify their passphrases/seeds.
Coinomi stated in their official announcement that the data they sent to Google API servers were not “processed, cached or stored”. Don’t take my words for it and let’s see what Google says in their terms:
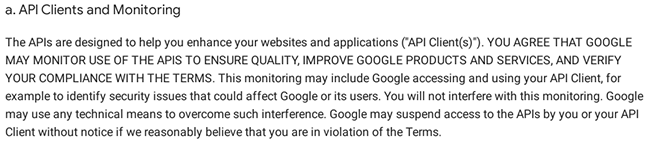
Based on our analysis, it can be concluded that the utilization of Google API to "spell check" users' passphrases/seeds was a hidden feature that was not disclosed in the "Terms of Use" that I agreed to before installing the application. Had I been aware of this feature, I would not have used the application unless my intention was specifically to enhance my passphrase vocabulary. The omission of this information deprived users of the opportunity to make an informed decision about the potential risks associated with using the application.
It appears that there is a need for a change not only in their CTO but also in their legal representation.
STAKE CRYPTO GAMBLING
First and foremost, the public disclosure of my support ticket is a blatant breach of my privacy as a client. It contained confidential information pertaining to my case, including my personal crypto-currency addresses and the destination crypto-currency addresses. Such sensitive information should only be accessible to the relevant authorities and the parties directly involved in the case.
Furthermore, it is perplexing that Coinomi would label me as a "blackmailer" in their official statement, considering the fact that I willingly provided them with my personal wallet passphrase/seed. If my intention were to engage in fraudulent activities, why would I voluntarily share such sensitive information with them? I am relieved that I transmitted my passphrase/seed through an encrypted channel, as it appears that they would have been willing to publish it otherwise.
Additionally, it is worth noting that Coinomi failed to upload the entire support ticket and conveniently deleted the portion where they acknowledged that my assets were indeed stolen. They also stated their intention to blacklist the addresses associated with the stolen assets, in an effort to prevent the perpetrator from utilizing the assets on exchanges. This selective deletion of information raises questions about their transparency and willingness to address the issue at hand:
https://avoid-coinomi.com/files/coinomi_support_ticket.png
You can download the full support ticket from here (sensitive information blurred):
https://avoid-coinomi.com/files/coinomi_support_ticket_full.png
BONPAY LOGIN
I will recap the events to understand why I was affirmative with my conclusion that my assets were stolen because of Coinomi wallet and not because any other reason:
- Downloaded and installed Coinomi wallet on 14th February 2019.
- Pasted Exodus wallet passphrase/seed into Coinomi's wallet on the same day.
- Opened a new Coinomi wallet with a different passphrase and transferred crypto assets from an exchange to the wallet.
- Crypto assets were stolen on 19th February 2019.
- The only compromised wallet was the Coinomi wallet where the Exodus passphrase was pasted.
- Multiple wallets on the same virtual machine were not affected.
- Assets in the new Coinomi wallet were not stolen.
Based on these facts, it is evident that the only wallet that was compromised was the Coinomi wallet into which the Exodus passphrase was pasted. This wallet had a vulnerability or feature that allowed spell checking of passphrases/seeds using Google API servers.
CASTWEET 交易所
The team behind Coinomi made significant efforts to mislead the community by disseminating false information. I have gathered several screenshots of their tweets to shed light on the questionable practices employed by the company and to provide the community with a clearer understanding of the nature of this organization:
KING MONEY EXCHANGES
In their official statement, Coinomi argued that they had received no reports of hacked Desktop wallets, using this as a justification. However, it is important to note that there have been multiple reports on Reddit of stolen assets from Coinomi wallets. Despite this, I would like to outline several reasons why I may have been one of the first victims of this incident:
- The Desktop wallet is new and it's less than 3 months old (announcement screenshot).
- Desktop users are a lot less compared to the mobile version of the wallet.
- To trigger the bug, the user has to restore his wallet.
- My address had decent amount of crypto assets that attracted the criminal who stole my crypto assets.
DIGNITY GOLD
It appears that the team behind Coinomi, particularly the management, is evading responsibility and operating in secrecy. I am providing a list of individuals involved so that the community can recognize them if they are associated with any future projects or if they decide to rename Coinomi to something like "Spell Checker." Their actions have had a detrimental impact on the cryptocurrency ecosystem, as they lack credibility and professionalism.
SOLIDUS AITECH LOGIN
Based on my second statement and the YouTube video I shared, I am confident that I have presented all the relevant facts and evidence to support my claims regarding the theft of my cryptocurrency assets. I have also provided clear evidence that demonstrates Coinomi's lack of credibility.
Since Coinomi continues to refuse to take responsibility for my loss, I have no choice but to pursue legal action against them. If they insist on taking the hard path, so be it.
To the person who stole my cryptocurrency assets, I want to convey this final message. The situation is escalating, and legal investigations will soon commence. You still have an opportunity to rectify your mistake and return the assets to the following addresses:
BTC:
1CtybEBttTMRuNwn4vbfcWurAJXDYX9Ntg
LTC:
LfiMHCpmef4MYsWu3fnNLsxcMxJJutQgsb
BCH:
qpqj7jl6uw3u8lsg28zcd06rcdfpashmfvyv9k2t90
ETH (including ERC20 tokens):
0xd87209d2118012C8021Ca5B8A4D3732906aa2770